Cortex-Analyzers – release 3.2
The 3.2.0 release of Cortex-Analyzers repository is available. It includes 13 new and updated connectors like CrowdSec, VirusTotal, EchoTrail, CheckPhish, Verifalia, Kaspersky Threat Intelligence Portal, ThreatMinder, PaloAlto WildFire, Bitcoin Abuse and more.

It’s been a long time since the last announcement related to a new release of Cortex Analyzers and Responders. The team was head down shaping TheHive 5. However, in the mean time, Cortex’s community did a great job, submitting new contributions for additional connectors.
We spent some time reviewing and testing them, and making sure things are documented. Even if we are not the authors, we do our best to fix bugs, improve existing Analyzers & Responders, and publish new ones.
In addition to new Analyzers, a feature has been added to the framework: extracted observables can now be enriched and contextualised using extra attributes like tags, IOC & sighting flags. VirusTotal & EmlParser are the first 2 Analyzers that benefit from this capability.
Newcomers!
A huge thanks to the community and particularly to Peter Juhas, Joe Vasquez, Joe Lazaro and CERT-ARKEA. Here is a summary of this release:
Analyzers
- IP-API by Peter Juhas (@pjuhas)
- CheckPhish by Peter Juhas (@pjuhas)
- Verifalia by Peter Juhas (@pjuhas)
- Bitcoin Abuse by Peter Juhas (@pjuhas)
- Kaspersky Threat Intelligence Portal by Peter Juhas (@pjuhas)
- ThreatMiner by Peter Juhas (@pjuhas)
- EchoTrail by Joe Lazaro (@joeslazaro-cdw)
- CISMCAP by Joe Lazaro (@joeslazaro-cdw)
- PaloAlto WildFire by Joe Lazaro (@joeslazaro-cdw)
- CrowdSec by CERT Arkéa (@CERT-ARKEA)
Responders
- SentinelOne Hash Blacklister by Joe Vasquez (@jobscry)
- Microsoft 365 Defender by Joe Lazaro (@joeslazaro-cdw)
- PaloAlto Cortex XDR by Joe Lazaro (@joeslazaro-cdw)
Updates
- Maltiverse Analyzer has been updated to support authentication to the remote service, by Jorge López Zarza (@jlopezzarza)
- SEKIOA analyzer report has been improved, by Raphaël Cohen (@Darkheir)
- EmlParser analyzer by StrangeBee
- VirusTotal analyzer, by StrangeBee
Let’s focus on improvements made on EmlParser and Virutotal analyzers.
Emlparser 2.1
Since version 2.0, EmlParser analyzer reports a rendered version of the HTML part, if included in the analyzed email. To make it possible, the program relies on a function named, wkhtmltoimage(), included in the wkhtmltopdf Python library.
The analyzer’s report now contains an image of the rendered HTML so that analyst can have an exact overview of the rendered html content, like seen in the mail client application; and without stepping on a mine!
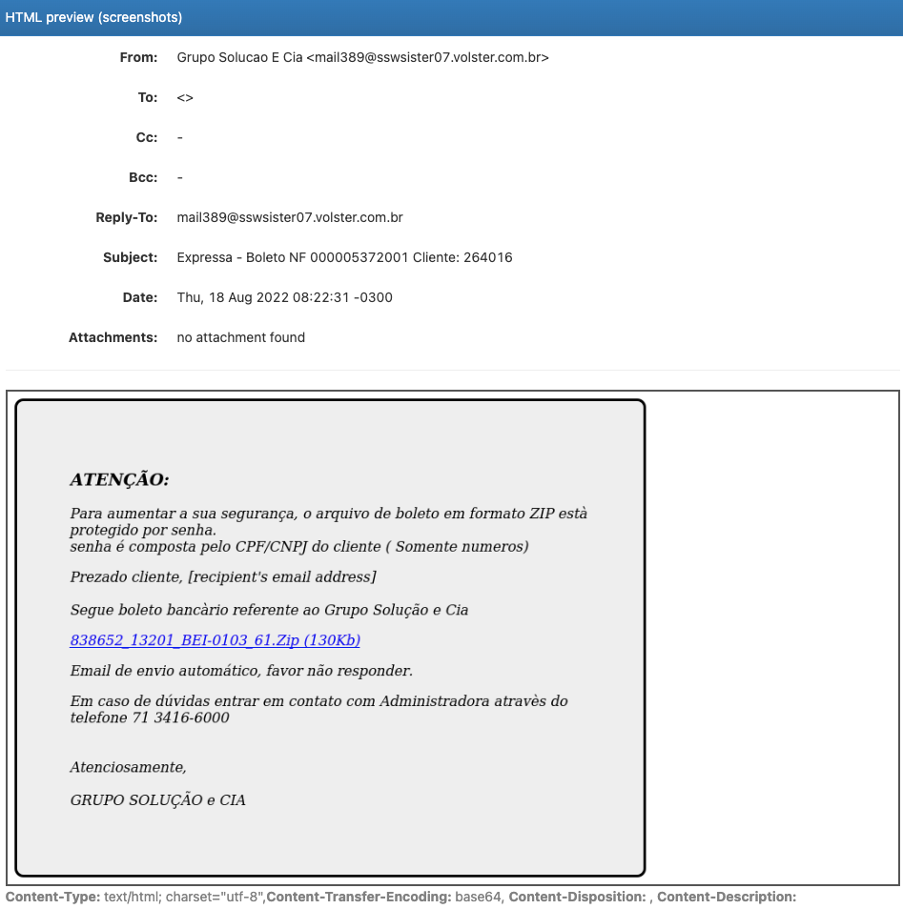
The version 2.1 has been improved in several ways.
- Firstly, the analyzer delivers a report even if the rendering fails for unexpected reasons
- Secondly, reported observables have been enriched with contextual tags. For example, a reported email address is now tagged with header:To or header:From. This is useful to quickly have the context in which it has been added. Same thing for IP address, domains/hostnames and URLs.
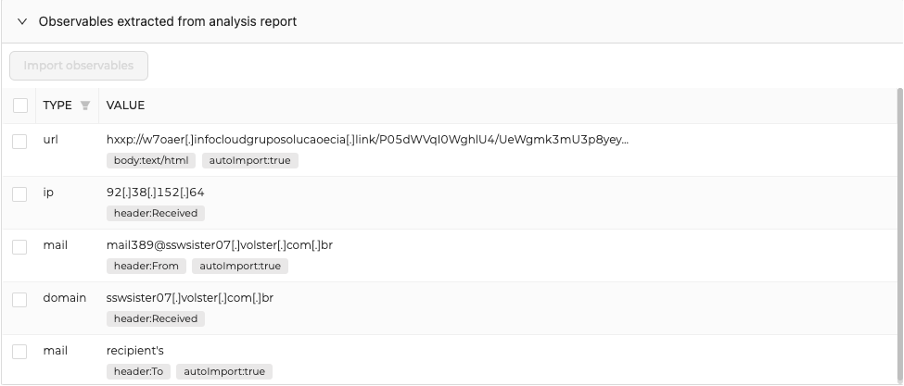
- Finally, you might notice a new tag named autoImport:true/fase is added to reported observables. We anticipated the next major version of TheHive, 5.1, so this tag not used yet; TheHive will use this tag to import some of them automatically on successful analysis. With Emlparser, URLs, attachments and email addresses will be imported automatically into the set of observables of the current Case ; ready to pivot on them and run new observables. Stay tuned!
The documentation related to this Analyzer has been updated, and can be found at: https://thehive-project.github.io/Cortex-Analyzers/analyzers/EmlParser/
VirusTotal 3.1
VirusTotal Analyzer has completely been reviewed and updated to use the version 3 of the API, with the help of the vt_api Python library. This was also the opportunity for us to enrich the report with useful information coming from from VirusTotal.
Most visible improvements can be seen in the long report below:
- The summary is enhanced, with a better overview of the detection rate
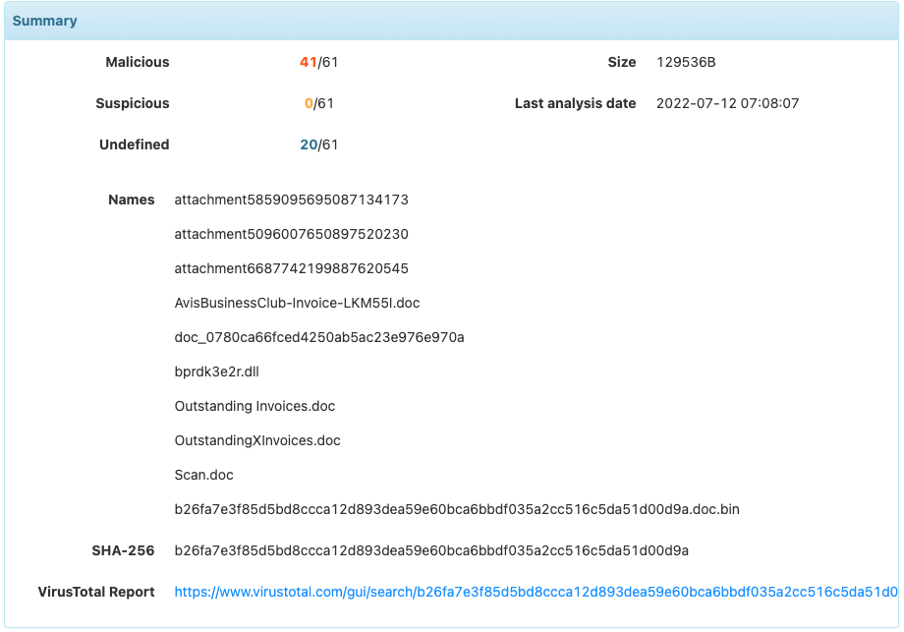
- Details of engines detection is still present, and has also been enriched
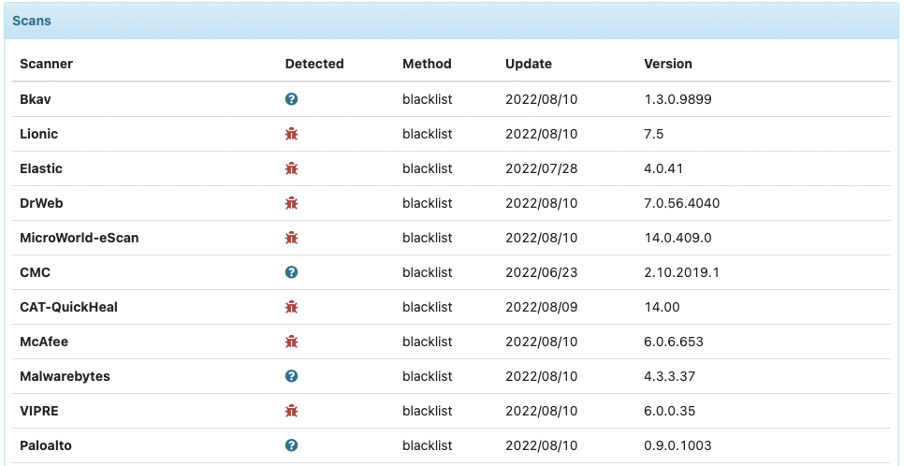
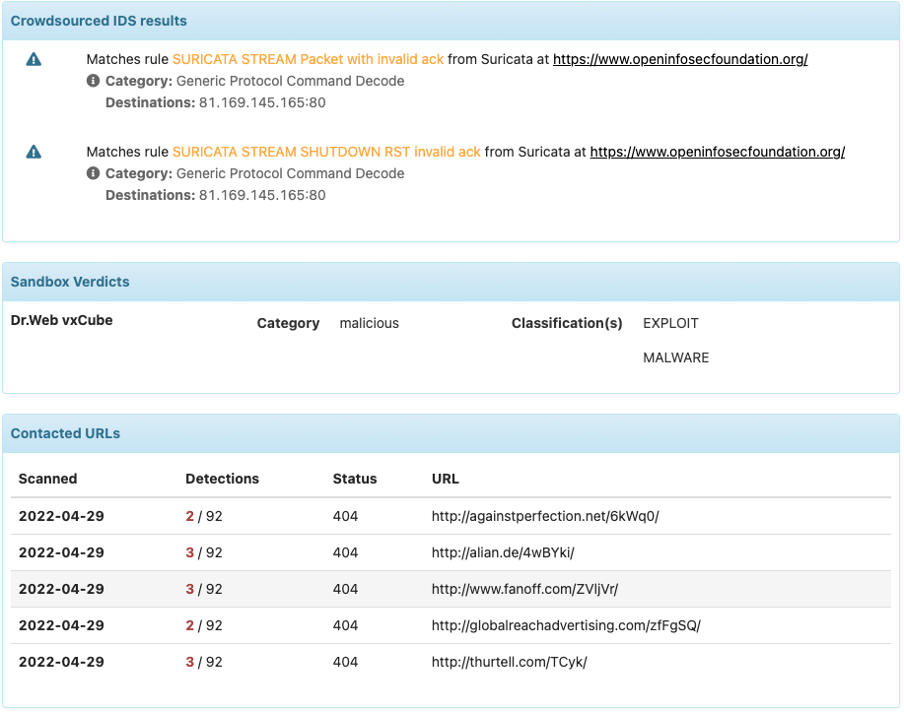
Depending on your API level of access, some useful extra information can be displayed:
- Yara rules
- IDS rules
- Sandbox verdicts
- Contacted URLs, IP & domain when available
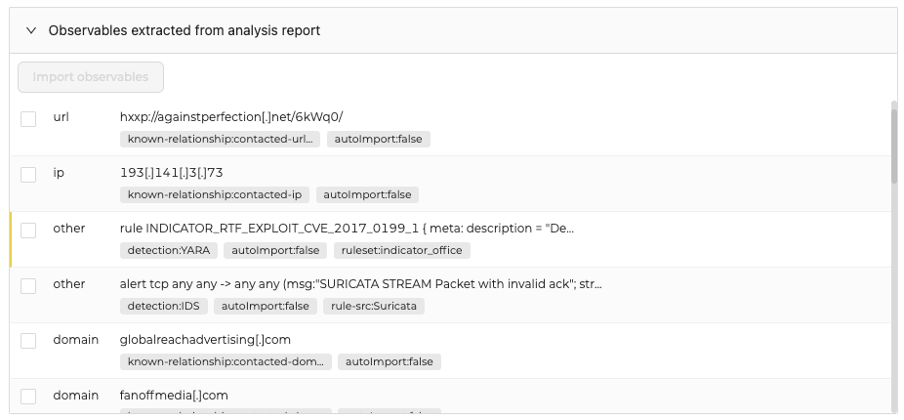
Extracted Observables
More observables are now extracted from the report and available to enrich the Case. IDS and Yara rules can be imported in the observables list as well.
Read more about this Analyzer at: https://thehive-project.github.io/Cortex-Analyzers/analyzers/VirusTotal/
Manage your own Analyzers and Responders
Since its version 2.0, Cortex can run Analyzers & Responders as Docker containers. Cortex uses catalogs to download the Docker images of public versions. Catalogs and images are maintained and built by StrangeBee.
There are great benefits to use these docker images:
- There is no need to worry about dependencies as they come with the images,
- A new container is used each time an Analyzer or a Responder is triggered (i.e. a new copy of the program)
Using Docker is easy with public Analyzers & Responders but what about your private connectors? Usually, they are run on the host, on which you need to install cortexutils library, and other dependencies.
To make it easier for you to manage your own docker images of your private connectors, we published a new tool named build-customimages.sh. This program builds and manages your own set of Analyzers & Responders.
It can be found there or in ./Cortex-Analyzers/utils/docker/build-customimages.sh.
Learn more in the dedicated documentation: https://thehive-project.github.io/Cortex-Analyzers/admin_guides/manage-private-custom-analyzers-responders/
How to update ?
Using programs on the host
If you are still using the old-style way of using analyzers and responders, run the following commands:
cd path/to/Cortex-Analyzers
git pull
for I in analyzers/*/requirements.txt; do sudo -H pip3 install -U -r $I || true; done
for I in responders/*/requirements.txt; do sudo -H pip3 install -U -r $I || true; done
Once done, make sure to refresh your analyzers and responders in the Cortex WebUI:
- Connect as an orgadmin and go to the Organization menu
- Click on the Analyzers tab and click on the Refresh analyzers button
- Do the same for the Responders tab: click on the Refresh responders button.
Refer to the online Cortex documentation for further details.
Using catalogs
You have nothing special to do. Cortex automatically fetches the updated catalog.
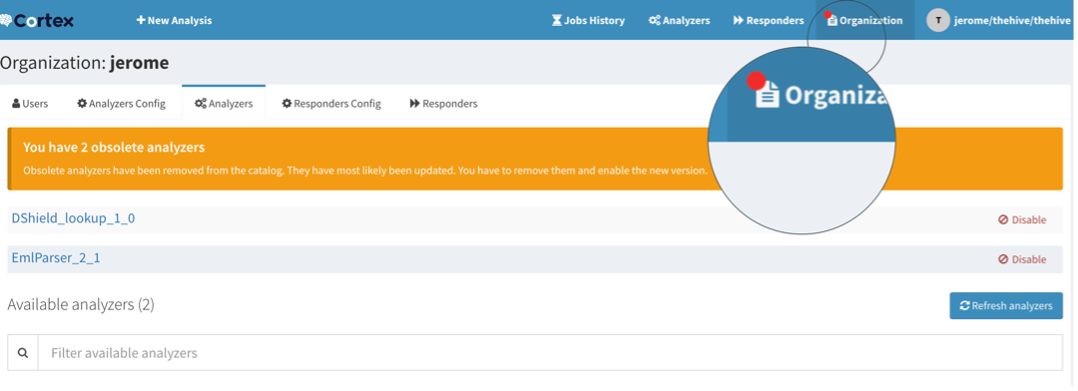
New if using TheHive > 5.0.14 and Cortex > 3.1.7, a notification might be displayed in TheHive and in Cortex meaning some operations are required in Cortex:
- TheHive notifies something happens in Cortex
- Log in to Cortex
- Update your configuration, notice the red badge meaning an action is required. Disable old versions, enable new ones.
Update Analyzers report templates
If you are using TheHive 5, you must import the new report templates in your instance.
If you’re using TheHive 4.1:
- download the updated package
- log in TheHive using an administrator account
- go to Admin > Analyzer templates menu
- click on Import templates button and select the downloaded file.
Need Support ?
Shall you encounter any difficulty, join our Discord community, or as a customer, contact StrangeBee’s support.
