Incident response and case management—stronger together
Give cyber threats no power over your systems. Learn why good case management is your best friend for robust incident handling and recovery.
Blood shortages, delayed surgeries and down computer systems. This is not a movie. It’s the result of a recent ransomware attack on several London hospitals.
Hospital officials say it could take weeks to recover. In the meantime, some of the staff have reverted to pen and paper—a risky way to manage patient outcomes. This is just one of the consequences organizations might face after being targets of cyber criminals in the modern world.
A cyberattack is not a matter of if, but when. It could be a data breach, ransomware or an employee succumbing to a social engineering event.
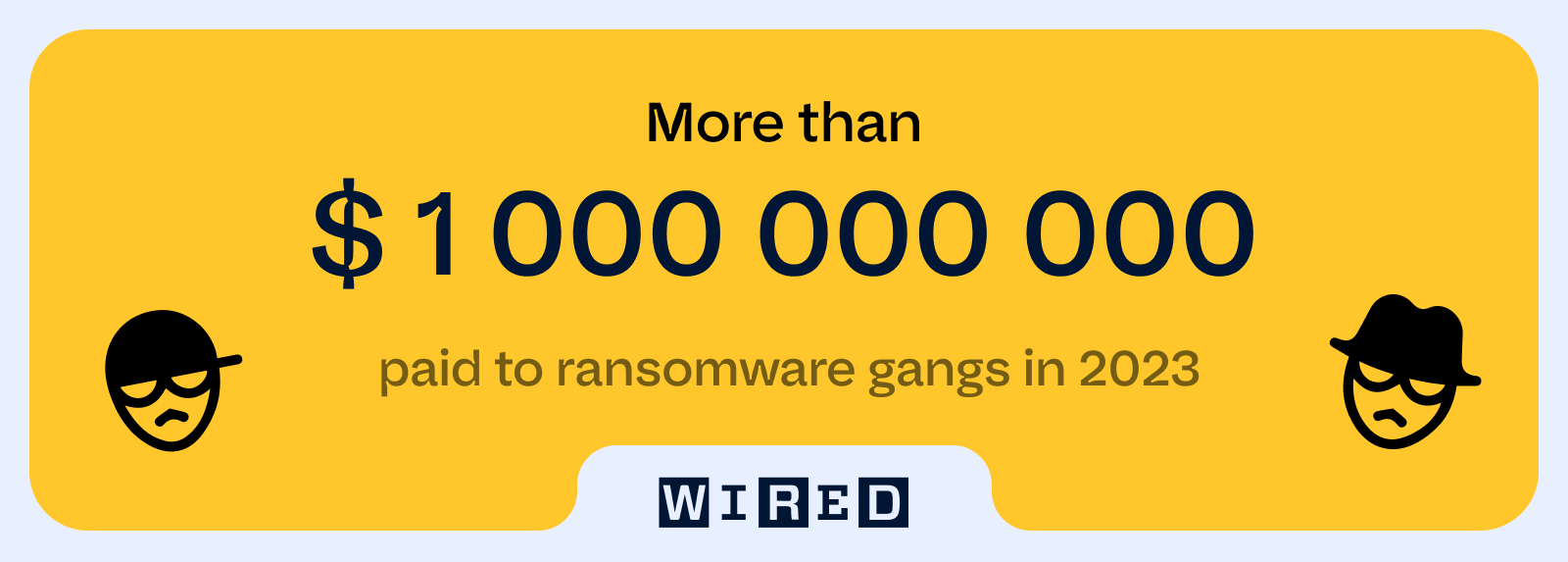
A report by J.P. Morgan Bank says that the evolving threat landscape now includes AI tools, nation-state attacks on critical infrastructure and increased social engineering attacks. Wired reports that more than $1 billion was paid to ransomware gangs in 2023.
If it’s online, it’s up for grabs: cloud vulnerabilities, supply chain infrastructure and IoT devices. The threat horizon is more ominous than ever.
Adopt a proactive incident response framework
In today’s daunting cyber risk landscape, organizations can defend themselves with a robust incident response strategy supported by good security case management practices.
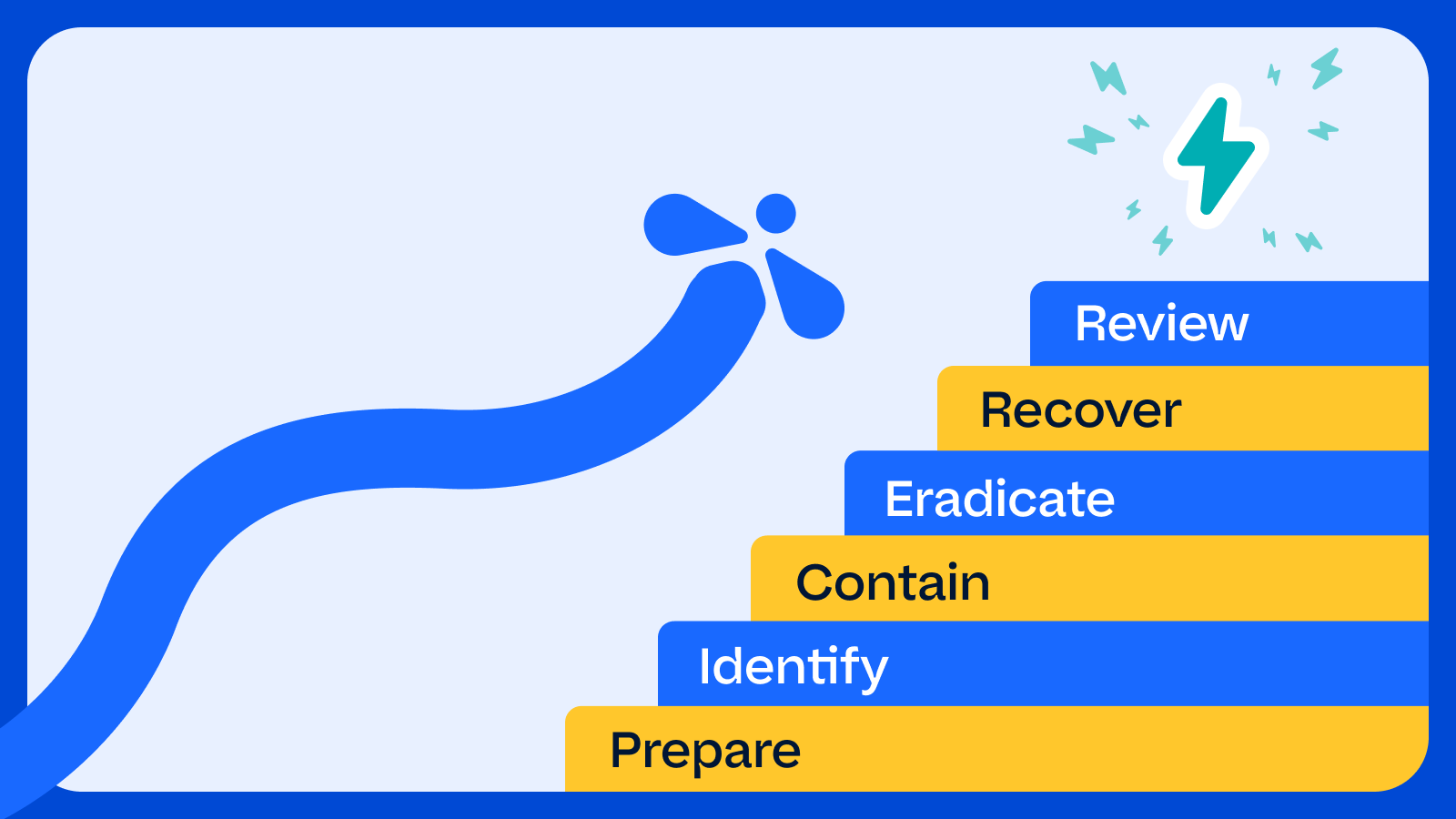
Let’s walk through the vital steps to consider, as presented in the recently updated (April 2024) National Institute of Standards and Technology (NIST) framework.
Incident response essentials: from preparation to recovery
Prepare
This is the foundation of incident handling. Enterprises and organizations must establish a complete Incident Response Plan (IRP). It defines roles, responsibilities, procedures, regular training and simulations for a proactive approach against cyber threats.
Identify
Tools like SIEMs and intrusion detection systems (IDS) are essential for rapidly detecting potential dangers. After this, you need quality triage. Here’s where it's vital to have an incident response platform with strong case management features.
Such platforms, like TheHive by StrangeBee, will facilitate rapid decision-making. They allow to easily prioritize alerts, log data and correlate events with comprehensive dashboards.
Contain
Now it's time for immediate action, such as disconnecting infected systems and network segmentation. Having quick responders, like in TheHive, will help you speed up threat containment.
It’s also essential to collaborate during containment. Security teams should be able to share updates in real time with live streaming, tracking containment efforts and facilitating collaboration.
Eradicate
Block malicious IPs, remove malware, backdoors and compromised credentials, and patch all known vulnerabilities. Your incident response platform should let you customize and create your own responses. This way, you can adapt it to your team’s playbook.
During eradication, everything must be tracked through case management. This will ensure a comprehensive record for stakeholders during and after incident resolution. Having a user-friendly, customizable timeline is essential here.
Recover
Returning systems to normal operations involves restoring backups, database and files. Verify system functionality with connectivity and application tests; update security settings to avoid unpredictable outcomes. Comprehensive performance, regression and security testing is a must.
TheHive's incident management supports seamless collaboration during recovery. It offers centralized communications that eliminate the need for random emails, separate chat channels and phone calls. Tasks can be assigned and tracked. Having everyone on the same page ensures an efficient recovery process.
Post-incident activities
Every incident is an opportunity for greater resilience. A dedicated platform like TheHive is like a ‘black box’ flight recorder. It captures all the communications, detailed logs and actions performed during incident response.
This thorough timeline reconstruction provides a comprehensive record for analysis and improvement. It also facilitates the creation of a revised and up-to-date IRP. With strong case management features, your platform will be a rich source of information for task reviews, performance analysis, metrics and reporting.
The case for case management platforms
Good case management provides a framework for efficient threat response, facilitating team communication, centralizing data, coordinating activities and preserving evidence.
All this is vital for high-level assessments, strategic planning, decisions and a focused analysis of incidents from a macro to micro point of view. And of course, such a comprehensive approach will make lives of SOC, CERT and CSIRT professionals much easier.
A dedicated incident response platform with strong case management capabilities will serve as your single pane of glass for collecting alerts, investigating them, establishing patterns and responding to uncovered threats. Instead of struggling with chaos, security teams will be able to coordinate and collaborate for optimal outcomes.
In a world where cyber threats are everywhere, having the right tools in place isn't just a good idea—it's a necessity. TheHive is designed to give you that edge.
Learn more on the official website:
