Transforming data overload into actionable intelligence
Learn how TheHive allows you to easily manage alerts, automate triage, reduce false positives and track incidents from start to finish for faster response.
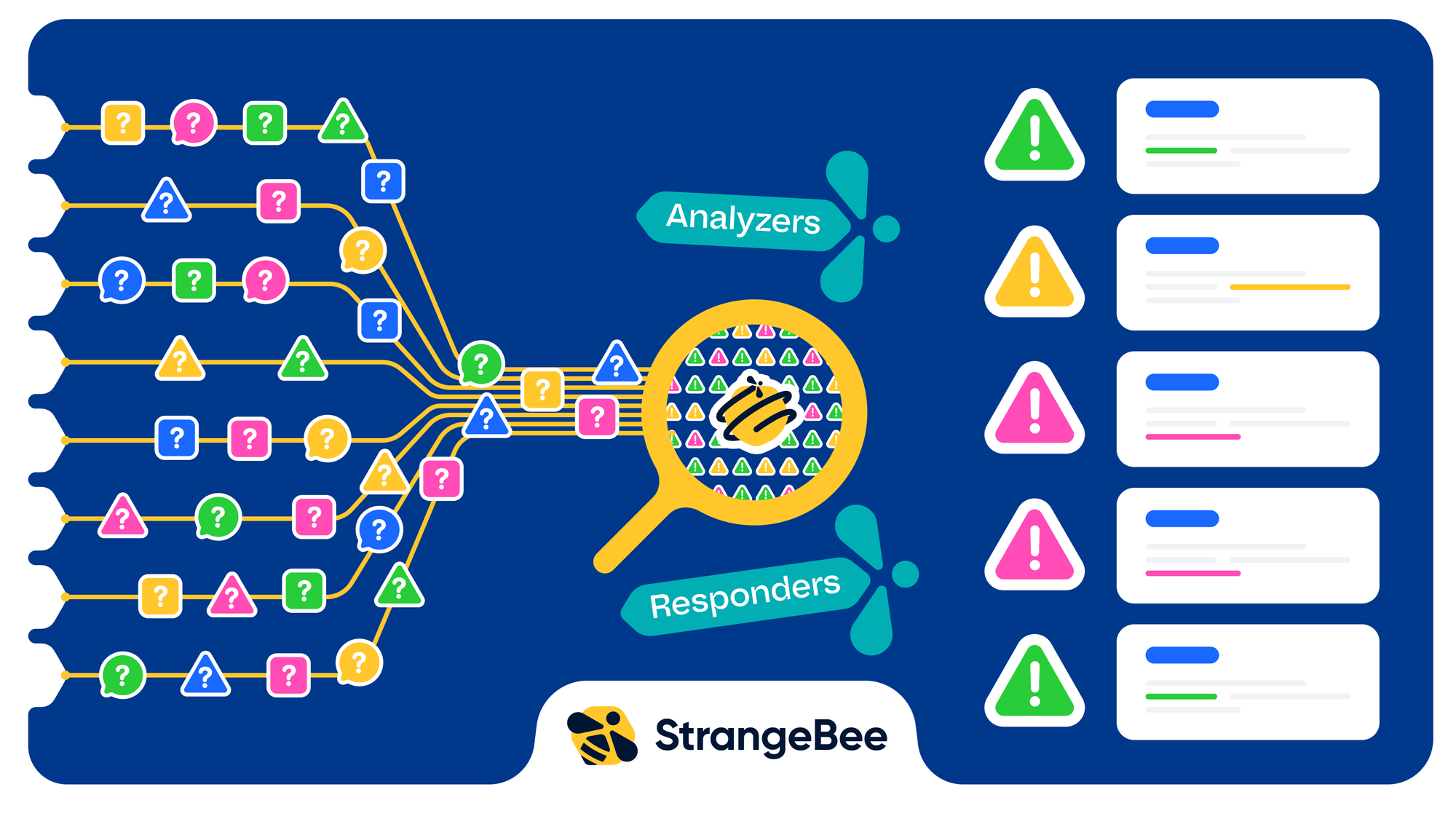
For seasoned cybersecurity professionals, receiving alerts is the easy part—the real challenge is managing the constant flood of data efficiently.
As modern threats grow more complex, filtering out false positives and correlating alerts from multiple detection systems (SIEM, IDS, EDR) becomes a strategic task in itself. Analysts need to go beyond just detecting threats—they must be equipped with tools that help spot, prioritize and act swiftly on the most critical signals.
In this article, we’ll explore how organizations can optimize their alert management strategies, reduce noise and enrich alerts with actionable intelligence—all while leveraging TheHive to transform raw data into targeted responses.
The evolution of alerts, from overload to precision
Alerts used to be simple: basic notifications when something suspicious occurred. But in today’s landscape, they’re data-rich indicators, often drowning teams in complexity.
Without the right processes in place, even the most advanced alerting systems generate an overwhelming amount of noise. Teams can easily be desensitized by irrelevant alerts, miss correlations or fall victim to alert fatigue.
Key challenges examples
- False positives: System file tampering alerts are triggered by routine system updates, leading to unnecessary investigations.
- Correlating multiple alerts: Firewall, SIEM and EDR each flag the same malicious IP—manually linking these slows down response time.
- Alert fatigue: Analysts spend hours sifting through repetitive alerts, only to miss a subtle data exfiltration warning buried in the noise.
TheHive addresses these challenges head-on by correlating, enriching and optimizing alert management—turning disjointed notifications into a clear, actionable story.
Improving and correlating alerts: seeing the bigger picture
Not all alerts are created equal, and treating them as such can spread your team too thin.
The key is enriching alerts with the right context and correlating them across systems to uncover the full story.
Example: Imagine a compromised login triggers alerts across your infrastructure. Your firewall flags abnormal outbound traffic from an unknown IP, your SIEM logs a successful login from an unusual location and your EDR detects data exfiltration from a critical endpoint.
Individually, these alerts might seem low priority:
- The firewall alert could be dismissed as routine network traffic.
- The SIEM alert could be seen as a legitimate user traveling.
- The EDR alert might appear to be a minor data movement.
But when properly correlated, TheHive can help stitch these data points together:
- The IP from the firewall is linked to a known malicious actor.
- The successful login suggests a compromised account.
- The data exfiltration indicates the attacker is attempting to steal sensitive information.
With TheHive, analysts can identify this as a coordinated attack, not isolated events. Instead of sifting through noise, correlation reveals the real threat—enabling faster, more targeted responses.
Optimizing triage
TheHive offers multiple ways to integrate threat detection tools, giving organizations flexibility.
Most teams use custom scripts, orchestrators or connectors to link tools directly with TheHive. Custom scripts offer tailored automation, while orchestrators optimize alert feeds from multiple tools. Now, in terms of detection systems, many of them have built-in connectors for easy integration.
These options provide adaptable solutions for automating alert intake.
For teams needing more granular control, TheHive also supports Functions, small JavaScript snippets that process inputs and interact with TheHive's APIs. For example, an IDS alert can trigger a Function that creates an alert in TheHive without middleware.
Once alerts are generated, analyzers can automatically enrich observables like IPs or file hashes by checking threat intelligence or historical data. This reduces manual work, letting analysts focus on critical threats faster.
How it works:
- When an observable (like a suspicious IP) is detected, TheHive can be configured to automatically trigger a series of analyzers that confirm the maliciousness of the data in real time. This may involve checking the IP against threat intelligence feeds, inspecting logs, or correlating it with previous incidents.
- By the time the analyst opens the alert, half of the investigation is already complete. The analyzers provide a detailed report of findings, allowing the team to focus immediately on deeper investigation and adequate response.
- This process significantly reduces manual workloads, helping analysts prioritize the most dangerous alerts and neutralize potential threats more quickly.
Closing the loop: tracking and resolving alerts efficiently
As mentioned earlier, timely detection is only the first step in proper security alert management. Ensuring each alert is fully resolved and accounted for is crucial to preventing any dangerous gaps in the process.
TheHive closes the loop on alert management, ensuring that every step of the process is tracked, from detection to resolution.
Key Features:
- Task Assignment and Escalation: As alerts are investigated, TheHive allows the assignment of tasks to the relevant team members and a detailed tracking of progress. If the incident escalates, it ensures that all stakeholders are informed and the response is coordinated.
- Alert Closure and Documentation: Once an alert has been handled, all actions and findings are logged within TheHive. This provides a complete audit trail for compliance and future reference.
- Leveraging Historical Data: Every closed alert is stored in TheHive’s searchable database. If a similar alert appears months later, analysts can pull up the historical data to see how it was handled, what steps worked, and how the threat was neutralized.
- Performance Monitoring with KPIs: TheHive also automatically computes KPIs such as MTTA and MTTR. This ensures that teams can continuously monitor their performance, identify gaps, and make adjustments in real time to meet their targets, maintaining a high level of efficiency throughout the alert management process.
By managing the entire lifecycle of an alert, TheHive empowers teams to not only resolve issues but also learn from past incidents, continuously improving their approach to security operations.
Final thoughts
Managing the sheer volume of modern cybersecurity alerts is a daunting task for even the most experienced teams. But with the right tools, this burden becomes manageable. TheHive doesn’t just help you detect alerts—it transforms them into actionable intelligence, allowing your team to automate triage, reduce false positives and resolve incidents faster.
In the next article, we’ll explore Observables and their pivotal role in security incident response, taking your detection and investigation capabilities to the next level.
Put TheHive to the test now!
Try TheHive Cloud Platform (SaaS)
Get in touch with us
As always, we welcome your feedback and suggestions, so please let us know what you think here.
